Alpine is a terminal email client.
Free and open-source.
Alpine is a terminal email client that I use with FastMail's email service. I hope this blog post will help people who use both and don't validate their SSL certificates.
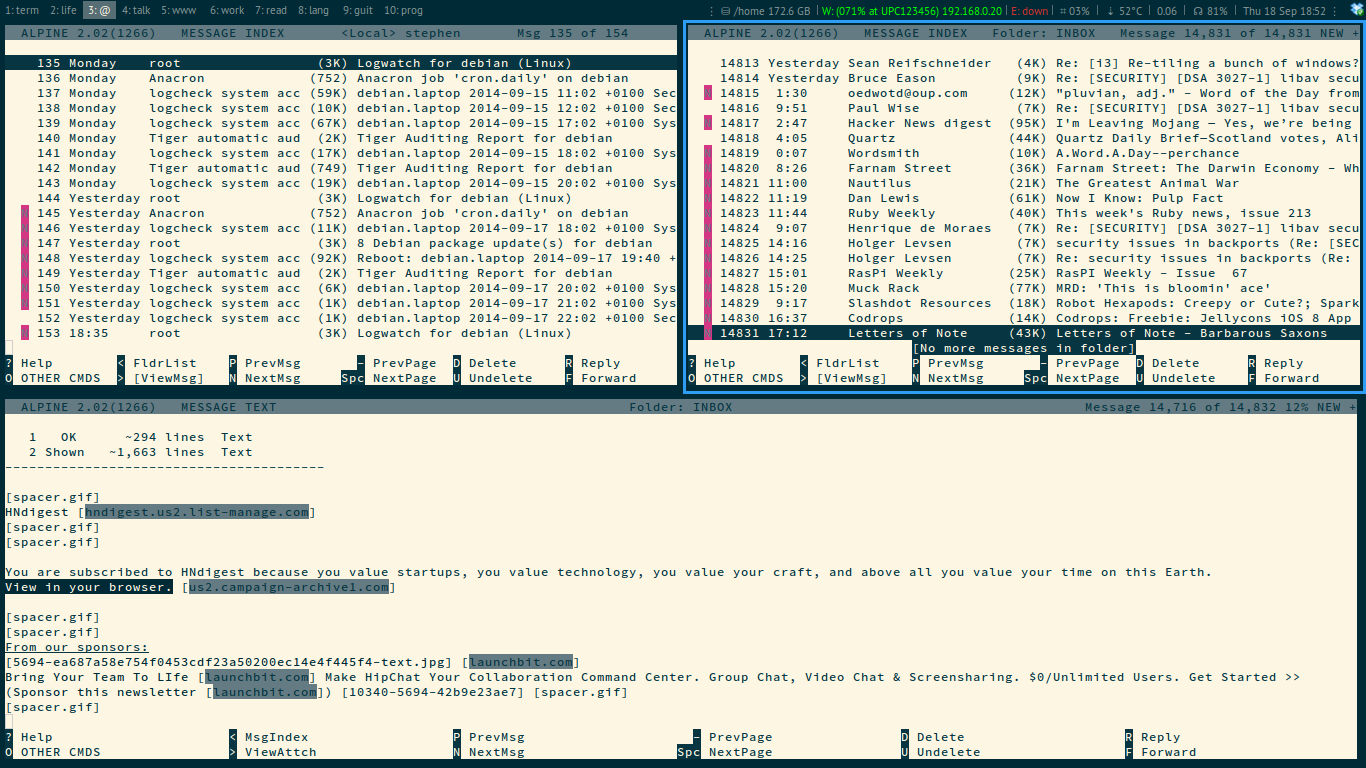 Tiling window manager with alpine
Tiling window manager with alpine
Looking at .pinerc files on GitHub and other places online for FastMail users you will see the following configuration:
# Syntax: optnl-label {optnl-imap-hostname}optnl-directory-path[]
user-domain=mail.messagingengine.com
inbox-path={mail.messagingengine.com/user=email@fastmail.fm/ssl/novalidate-cert}INBOX
folder-collections={mail.messagingengine.com/user=email@fastmail.fm/ssl/novalidate-cert}INBOX.[]
The interesting part.
In the above configuration you can see a novalidate-cert after ssl. With this configuration a connection is made to FastMail's server via SSL, but the certificate is not validated; it provides encryption but not authentication. Your connection will be encrypted, so no plain text for coffee shop packet sniffers, but you can't be sure it is FastMail's server you are connecting to. This exposes you to a MitM (man-in-the-middle) attack.
What you would would like to see is:
# Syntax: optnl-label {optnl-imap-hostname}optnl-directory-path[]
user-domain=mail.messagingengine.com
inbox-path={mail.messagingengine.com/user=email@fastmail.fm/ssl}INBOX
folder-collections={mail.messagingengine.com/user=email@fastmail.fm/ssl}INBOX.[]
Getting our certificate
If you try to use the above configuration without taking some additional steps you will encounter an error. I is likely why novalidate-cert is so common. To make this work we need to grab of copy of FastMail's SSL certificate to store locally. We can use OpenSSL to accomplish this.
vim as your default email editor
 Composing an email with vim
Composing an email with vim
openssl s_client -connect www.fastmail.fm:443
This will output a lot of certificate related information, most of which we don't need. The part which begins -----BEGIN CERTIFICATE----- and ends with -----END CERTIFICATE----- is what we need to copy. Copy this to a .pem file such as mail.fastmail.fm.pem. This is a temporary name; we need to determine the hash value of this certificate to rename it appropriately. Hash values are used for naming so that matching certificates can easily be found on your system. We can use OpenSSL to find our hash value.
openssl x509 -in mail.fastmail.fm.pem -hash -noout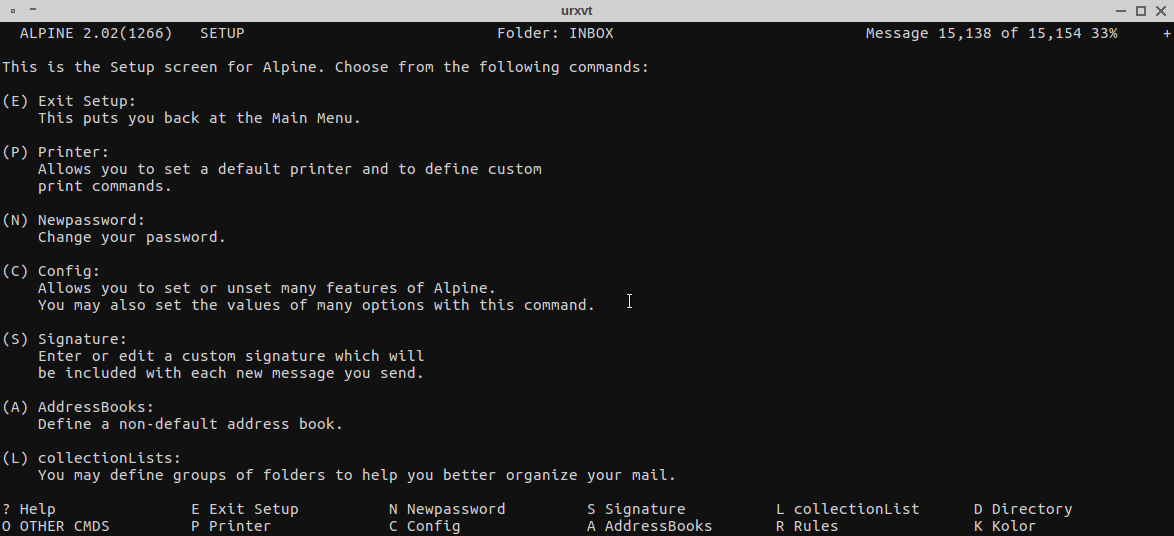 Alpine can also be configured from inside
Alpine can also be configured from inside
This will return an 8 character hash value such as 'e656db79'. This is what we will name our .pem file but with one alteration. We will add a suffix; a number indicating whether or not we have more than one copy of this certificate. It is likely this will be the first copy so in this case we will append a 0 to the name forming e656db79.0.
Moving the certificate to the right location
Now that we have our certificate with the correct name, we need to place it in the appropriate directory. To find out where OpenSSL stores certificates on your system, use the following command:
openssl version -dOn Debian certificates are stored in /usr/lib/ssl. Once you have moved the certificate to your SSL certificates directory and start alpine you should be greeted with a login dialog.
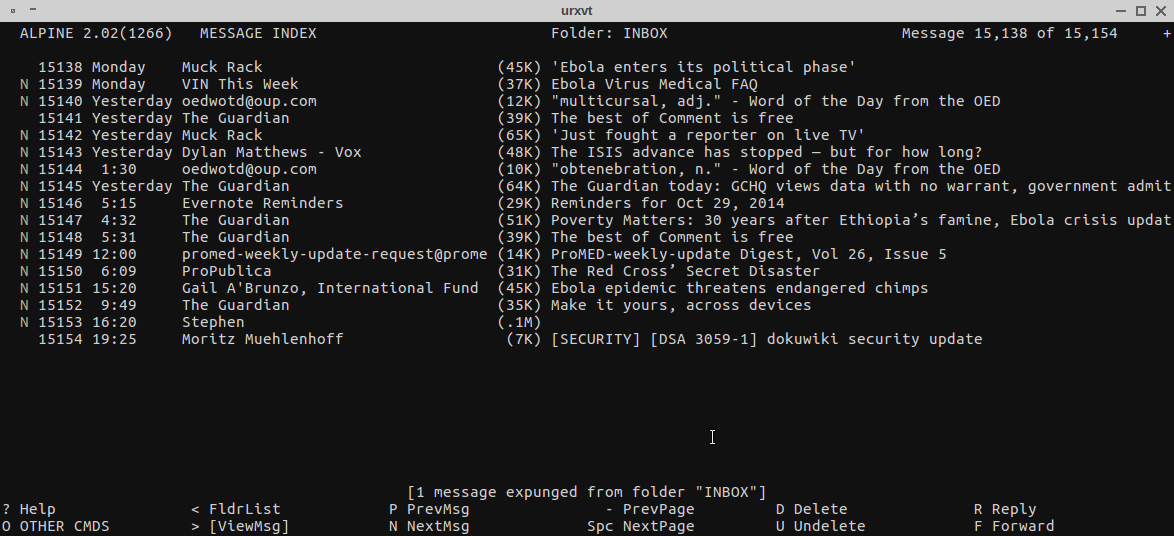 My inbox in Alpine
My inbox in Alpine